Blockchain seems complicated, and it definitely can be, but its core concept is really quite simple. Don’t be spooked by the technobabble that people use to describe “blockchain.” A blockchain is just a database. In simple words – A Blockchain is like a diary that is almost impossible to forge or tamper.
In Technology terms – a Blockchain can be defined as a chain of blocks that contains information. Each block in a blockchain is cryptographically linked to the last entry. In plain English, each new entry must contain a sort of digital fingerprint(hash) of the last one. And that’s it! Since each fingerprint points back to the last one, you end up with a chain of blocks; and hence the name – Blockchain.
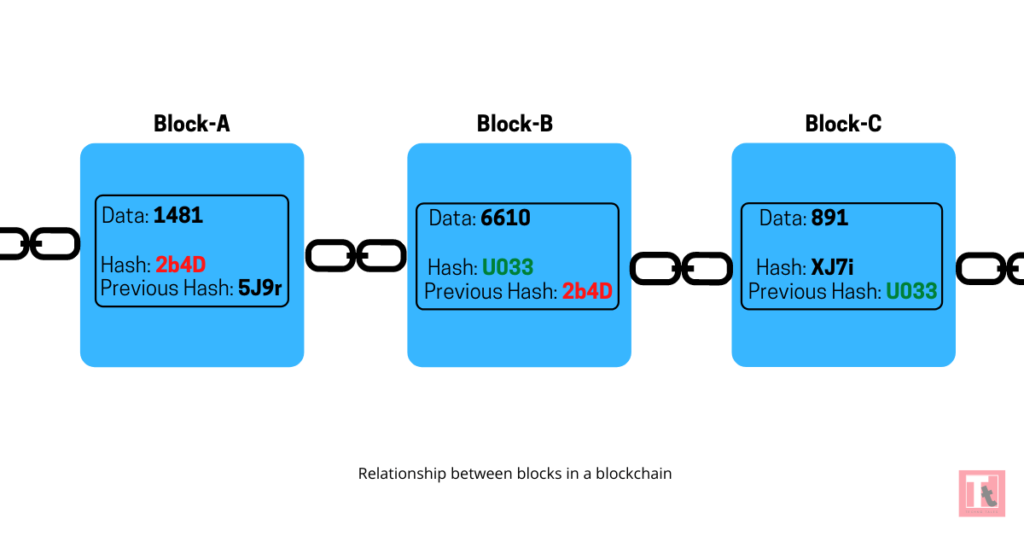
A blockchain is immutable: if you change a block(i.e. Data), it changes the fingerprint(Hash) automatically. And since that fingerprint is included in the next block, the next block is changed too. So ultimately you end up with a domino effect where any change becomes evident. So you can’t alter any information without everyone noticing.
Blockchain – A Real Life Example
To explain how a Blockchain network really works, let me give you a real life example:
Let’s imagine that 5 people in a room decide to make a separate currency. They have to follow the flow of funds, and gave the responsibility to maintain the records to one person – say Dan. So Dan decided to keep a list of all actions in a diary:
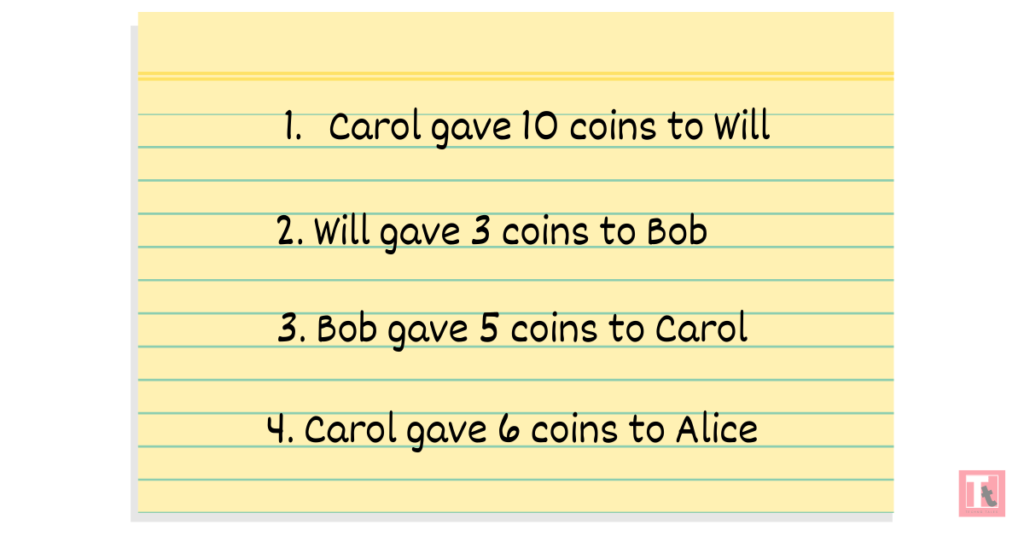
Say Bob decided to steal money. To hide his act, he changed the entries in the diary:
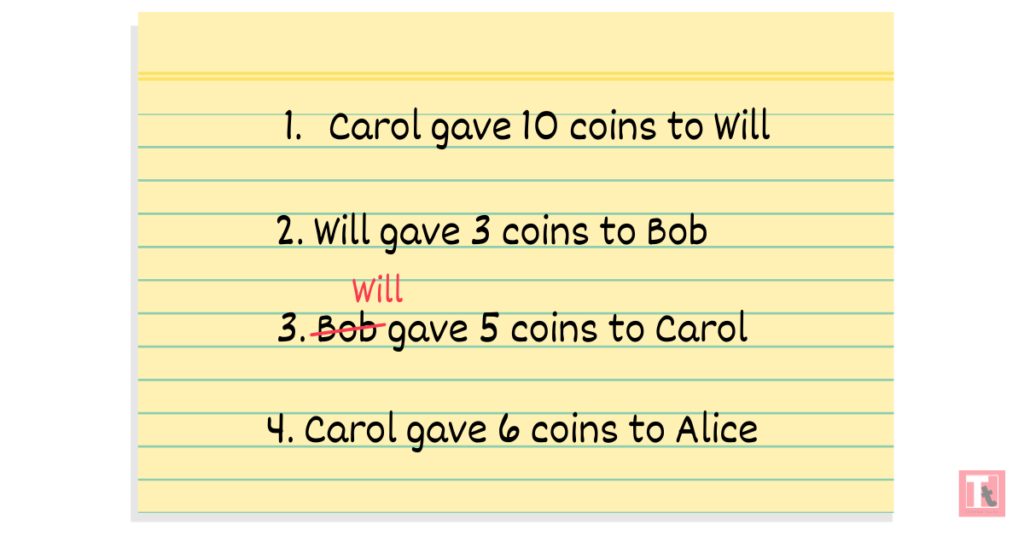
Dan noticed that someone had changed the entries in his diary without his knowledge. So he decided to stop this from happening. So he found a program called a “HASH FUNCTION” that turns text into a set of numbers and letters as in the table below.
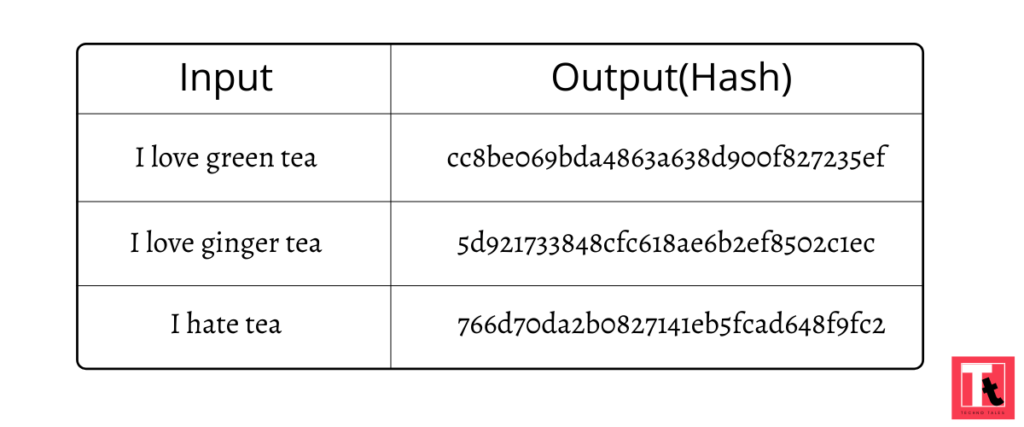
A hash is a string of numbers and letters, produced by hash functions. A hash function is a mathematical function that takes a variable number of characters and converts it into a string with a fixed number of characters. As you can see in the above example, when I changed the string “green” to “ginger”, it created a completely new hash.
So Dan inserted a hash, after each record. The new entries in the diary was as follows:
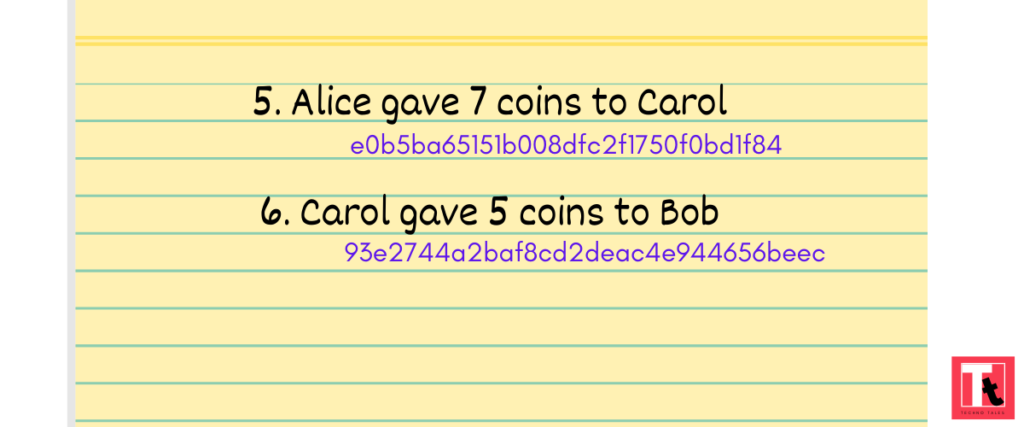
Bob decided to change entries again. At night, he got to the diary, changed the record and generated a new hash.
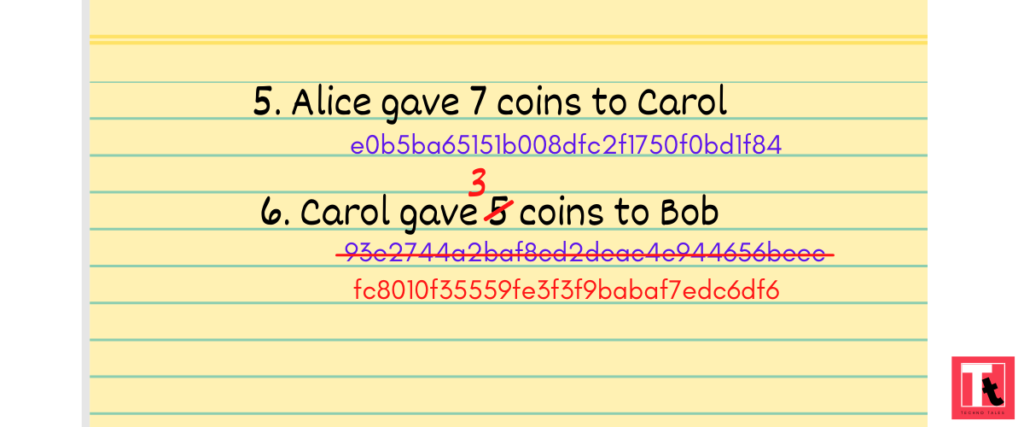
Next morning Dan noticed that someone has again modified his diary. He was furious but giving up is not in his nature. So he decided to further complicate the record of each transaction. After each record, he inserted a hash generated from the record PLUS last hash. So this way each record now depends on the previous record.
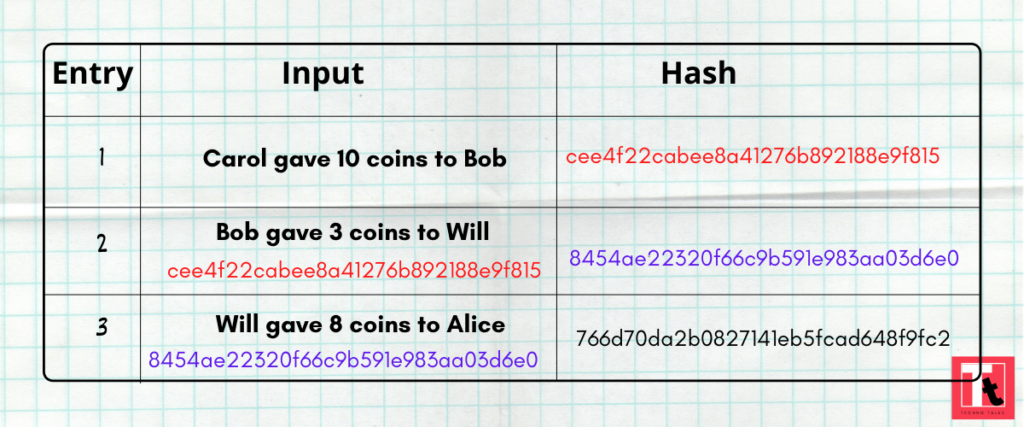
Now if Bob tries to change any record, he will have to change the hash in all previous entries. Otherwise the entire chain of (linked)transactions will become invalid. But Bob is really desperate for more money, so he spent the whole night counting all the hashes.
But Dan did not want to give up. He decided to add a number after each record. This number is called “NONCE”. Nonce should be chosen so that the generated hash ends in two zeros.
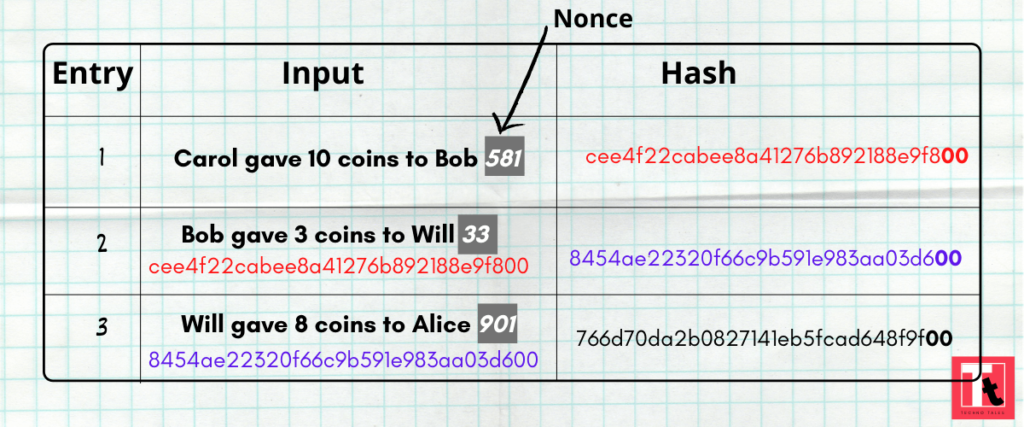
The trick of Dan to add Nonce at the end of each entry made the task of forgery a real nightmare for Bob. Because now to make any unauthorised change in the diary entries, Bob would have to spend hours and hours choosing Nonce for each line. And more importantly, finding the correct Nonce is a difficult and time consuming task, not only for human being, but also for computers.
Dan is relaxed and tension-free now as he is confident that no one will mess with his diary records.
But very soon Dan realized that there were too many records and that he couldn’t keep the diary like this forever. So he wrote 1,000 transactions and converted them to one page spreadsheet. Carol checked and validated that all transactions were valid & legitimate. Now Dan spread his spreadsheet diary over 5,000 computers, which were all over the world. These computers are called NODES. Every time a transaction occurs it has to be approved by these nodes(computers), each of whom checks its validity. Once every node(computer) has checked a transaction there is a sort of electronic vote, as some nodes may think the transaction is valid and others think it is a fraud. Now each node has a copy of the digital ledger or Blockchain. Each node checks the validity of each transaction. If a majority of nodes say that a transaction is valid then it is written into a block.
Now, if Bob change one entry, practically it means he actually modifies the record on only ONE node(computer), remaining all the other nodes(i.e. 4999 computers in this case) will still have the original hash of the record. They would not allow the change to occur. This way the mechanism prevents fraud and ensure data integrity.
The spreadsheet made by Dan which contains 1000 transactions is called a BLOCK. Please note that 1000 is just a reference figure. The whole family or collection of blocks is the Blockchain. Every Node(computer) has a copy of the Blockchain or Ledger. Once a block reaches a certain number of approved transactions then a new block is formed. The Blockchain updates itself automatically after a fix interval of time(for example, every 10 minutes). No master or central computer instructs the computers to do this.
Lastly you can only APPEND a Blockchain. You can not update or delete an EXISTING transaction in a Blockchain. As soon as the ledger or blockchain is updated, it can no longer be changed. Thus, it’s impossible to forge it. This is a big difference between a traditional relational database(RDBMS) and a Blockchain.
In a nutshell, that is all about “How a Blockchain Works”.